The Helium Network is a decentralized network that aims to create a decentralized Internet of Things (IoT) network using blockchain technology. The network utilizes a new type of consensus mechanism called "Proof of Coverage" which allows anyone with a small amount of hardware to participate in the network and earn rewards for providing network coverage.
One of the key features of the Helium Network is its built-in Denylist, which is a mechanism for preventing spam and abuse on the network. The Denylist is a decentralized list of addresses that have been flagged for spamming or other malicious behavior. These addresses are then prevented from participating in the network and earning rewards.
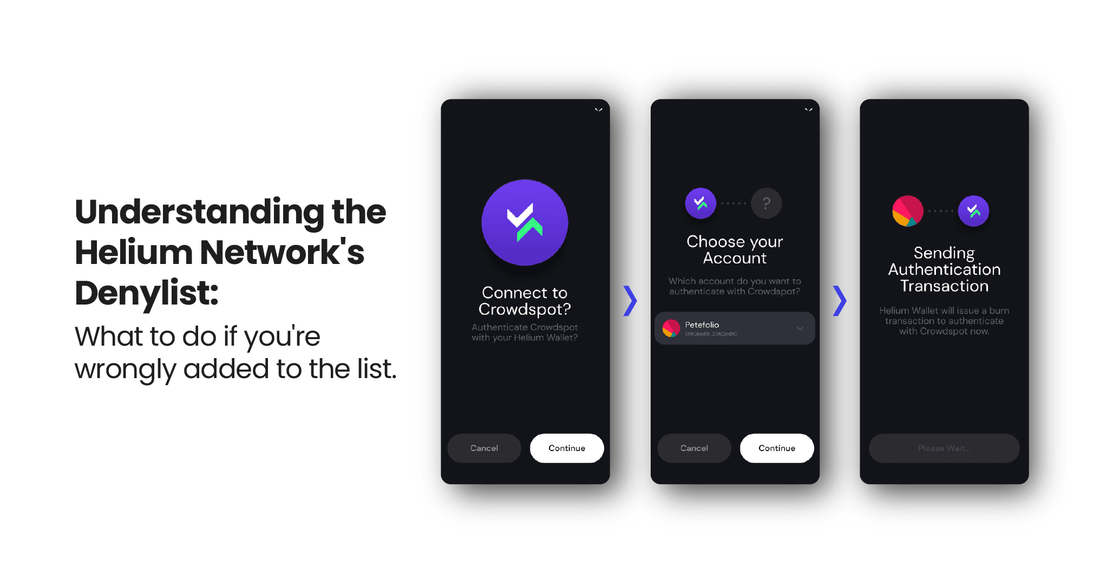
Recent reports have surfaced of individuals being added to the Helium Network's Denylist without justification. This includes individuals who have not engaged in any actions that would be considered trying to exploit the system. If you have been added to the Denylist mistakenly, you can submit a request for removal through the following link: https://docs.helium.com/mine-hnt/denylist-removals
The Helium hotspot denylist is a community-driven blacklist which any member of the network can submit additions to if suspected of "gaming" or "spoofing" fraudulent reporting of location. You can read more about it here.
The Denylist is an important tool for maintaining the integrity of the network and ensuring that it remains a useful and reliable resource for IoT devices. It helps to prevent spamming, which can overload the network and make it difficult for legitimate devices to communicate. It also helps to prevent malicious actors from using the network for nefarious purposes, such as launching DDoS attacks or stealing personal data.
The Helium Network's Denylist is maintained by a decentralized group of validators, who are responsible for identifying and flagging addresses that are engaging in malicious behavior. These validators are incentivized to maintain the integrity of the network by earning rewards for their work. You can also see the Denylist updated in real-time via Hotspotty.
One of the benefits of the Denylist is that it is not controlled by any single entity, making it difficult for malicious actors to manipulate or circumvent. This ensures that the network remains a fair and open resource for all users.
Another benefit of the Denylist is that it is transparent and auditable, allowing anyone to see which addresses have been flagged and why. This helps to promote accountability and trust in the network and ensures that the network can respond quickly and effectively to changing threats.
Overall, the Denylist helps maintaining the integrity and security of the network. It helps to prevent spamming and abuse, ensuring that the network remains a reliable and useful resource for IoT devices. Its decentralized, transparent, and customizable nature ensures that the network remains fair, open, and accountable for all users.
In conclusion, the built-in Denylist is a powerful tool that helps to prevent spam and malicious behavior, maintaining the integrity of the network. It is decentralized and transparent which ensures fairness, openness and accountability.